 |
Preferred IT Group
Education Series . Preferred Care Spam Control, powered by Reflexion Lesson 5 - Address On The Fly |
 |
|
Topics covered in
this lesson:
1. Address-On-The-Fly |
A-O-T-F |
What's all the fuss? Since you have given this special email address to merchant1, you noticed that you have started to receive some emails from a different company that you have never dealt with before. In an earlier lesson we learned about the email footer attached to the bottom of each email. In this footer you will see information about the sharing of your protective address. This example shows that merchant1, the trusted vendor, shared your email address with merchant2 whom you have no idea about.
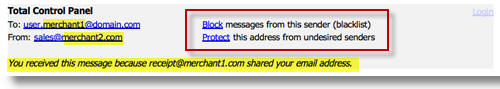
Selling email addresses is very common in the market place, and now we have a way to really see who we can trust and not trust. Within the email footer you will also see ways to control this. We can instantly block either or both parties, or protect this address allowing it only to come from the desired party.
Very useful if you deal with mail order companies, or various vendors on a daily basis.
| 2. Optional Feature - RADAR Reflexion, archiving, discovery and recovery | |
|
eDiscovery is
becoming an important tool for businesses that do transactions
via email. For more information on eDiscovery,
click here.
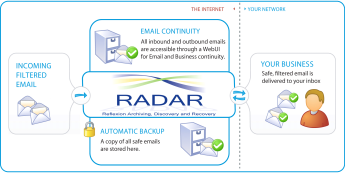
“In-The-Cloud” Gateway
Delivered as a hosted service, RADAR is easy to deploy and
operates seamlessly as a gateway to your existing IT
network.
Comprehensive Archive
All inbound and outbound email and attachments are indexed,
encrypted and stored in real time for rapid access.
eDiscovery Tools
eDiscovery Tools
With powerful email discovery tools, including our exclusive
DeepLink™ technology, users can instantly search the archive
for any email or attachment, with very fast results.
Email Recovery
Customized email “packaging” allows users to recover their
search results from the active archive back to their Inbox.
Email Continuity
An integrated webmail client enables users to access the
RADAR archive 24x7 from any location to ensure continued
access to email during power failures or in-house server
outages.
|
 |
 |
|
Radar is an available
add-on service and can be enabled per user. Call if you would like
a demo or more information.
Coming Soon -
Email Encryption
|
|
Columbia City
- 260.213.42666 |
 |
|
All rights reserved. |
||
